Proxim Wireless Security and Vulnerability Information
Proxim Wireless Security Vulnerability Policy
This policy is intended for customer guidance and information in the event of a reported vulnerability in a Proxim product. It is essential to ensure that Proxim customers have a consistent, unambiguous resource to help them understand how Proxim responds to events of this nature.
Reporting or Obtaining Support for a Suspected Security Vulnerability
Individuals or organizations that are experiencing a product security issue are strongly encouraged to contact the Proxim Technical Assistance Center (TAC). Proxim welcomes reports from independent researchers, industry organizations, vendors, customers, and other sources concerned with product or network security. The minimal data needed for reporting a security issue is a description of the potential vulnerability.
General Security-Related Queries
For general security concerns about Proxim products, the Proxim TAC can provide configuration assistance and technical assistance with security concerns. The TAC can also help with nonsensitive security incidents and software upgrades for security bug fixes. Use the following information to contact the Proxim TAC.
Proxim Technical Assistance Center
USA and Canada Toll-Free:
+1 866-674-6626 International: +1 408-383-7700
Business Hours:
Tier 1 / Tier 2 support: 24×7 live response
Tier 3 support: 8 a.m. to 5 p.m. M-F PST (UTC/GMT -7 hrs)
Commitment to Product Security and Integrity at Proxim
Proxim product development practices specifically prohibit any intentional behaviors or product features designed to allow unauthorized device or network access, exposure of sensitive device information, or a bypass of security features or restrictions. These include:
- Undisclosed device access methods or “backdoors”
- Hardcoded or undocumented account credentials
- Covert communication channels
- Undocumented traffic diversion
- Proxim Product Security Incident Response Process
The following points illustrate the Proxim process at a high level and provide an overview of the vulnerability lifecycle, disclosure, and resolution process.
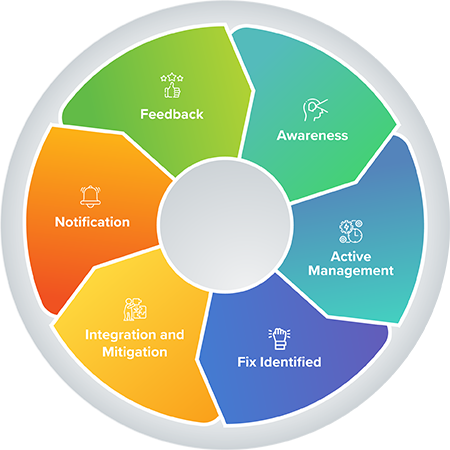
- Awareness: Proxim receives notification via the TAC of a security incident.
- Active Management: Proxim prioritizes and identifies resources.
- Fix Identified: Proxim coordinates fix.
- Integration and Mitigation: Proxim engages experts and executives.
- Notification: Proxim notifies all customers registered with the Vulnerability Mailing List.
Register for Proxim Security Vulnerability Notifications
Please fill out the form below if you wish to receive vulnerability and resolution emails for Proxim products.
